What is smishing? How to defend it
Discover what smishing is—a form of cybercrime using deceptive text messages to steal sensitive information. Learn how to protect yourself from these scams.
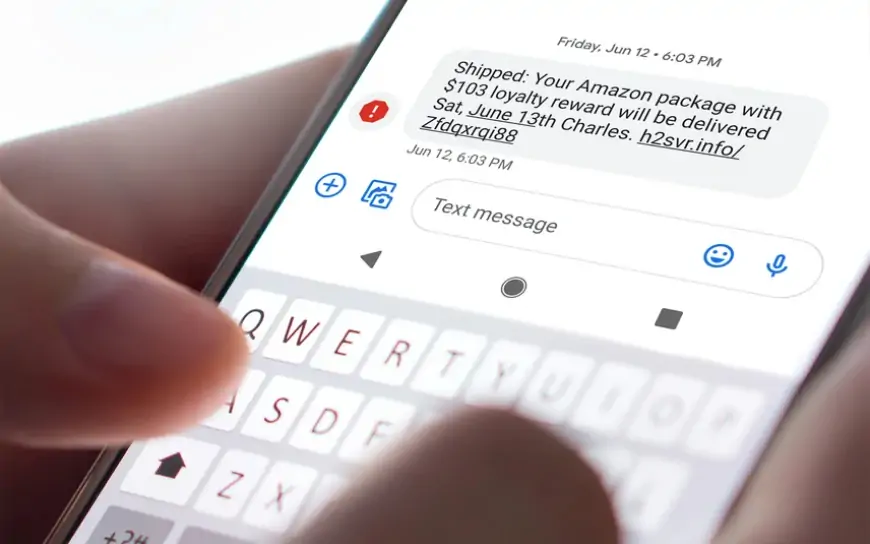
Understanding smishing
In today's mobile-driven world, cybercriminals have developed sophisticated tactics to exploit unsuspecting users, one of which is smishing. Short for "SMS phishing," smishing is a malicious strategy that deceives individuals through text messages, aiming to extract sensitive information or install harmful software.
This article explores the concept of smishing, providing real-world examples and offering crucial advice on how to protect yourself. By learning about smishing and staying alert, you can strengthen your defenses against this emerging cyber threat and safeguard your personal and financial security.
Smishing, a blend of "SMS" and "phishing" refers to a cybercrime where fraudulent text messages are used to trick victims into revealing personal information, such as bank account numbers, credit card details, and login credentials.
Similar to phishing emails, smishing aims to steal private data for identity theft, financial fraud, or other criminal activities. With the widespread use of text messaging, smishing has become a significant cybersecurity concern. For more insights into phishing, its mechanisms, and how to recognize these attacks, continue reading.
Smishing vs. Phishing
While both smishing and phishing are types of cyberattacks designed to steal personal information, they differ in their delivery methods and the platforms they target.
Phishing
Phishing is a broader term encompassing various deceptive communication techniques used to trick recipients into sharing sensitive information, such as usernames, passwords, credit card numbers, or Social Security numbers. Phishing attacks typically occur via email, where the attacker sends a message that appears to be from a legitimate source. The email usually contains a link to a fake website that mimics a trusted site, prompting the recipient to enter their private information.
Smishing
Smishing is a specific type of phishing that utilizes text messages (SMS) instead of email. In a smishing attack, the scammer typically impersonates a credible institution like a bank, service provider, or well-known company. The text message often creates a sense of urgency or threatens negative consequences if the recipient does not respond quickly. These messages may include links to fraudulent websites or trigger the download of malware onto the victim's device, leading to the theft of personal information.
To protect yourself, it's crucial never to share personal details in response to unsolicited messages, whether via email or text. Always verify any requests through known and trusted channels.
Common smishing tactics
Smishing attacks come in various forms, each designed to deceive victims into revealing sensitive information or taking actions that benefit the attacker. Here are seven prevalent types of smishing attacks:
- Impersonation scams: Attackers masquerade as a trusted organization or individual, sending messages that appear to be from a bank, government agency, or well-known company.
- Tech support scams: Scammers pose as tech company representatives, claiming that the victim's device or account has been compromised, and request sensitive information to resolve the issue.
- Account suspension scams: These messages falsely inform the victim that one of their accounts (such as a bank or social media account) has been suspended, prompting them to verify their identity by providing personal details.
- Missed delivery scams: Attackers send messages stating that the victim has missed a package delivery and must provide personal information or pay a fee to reschedule.
- Prize or lottery scams: These messages claim the recipient has won a prize or lottery, requiring them to provide personal details or make a payment to claim their winnings.
- Charity scams: In these schemes, scammers pretend to represent a charitable organization, often following a major disaster or during the holiday season, and ask for donations.
- Malware link scams: Messages that contain a link, which, when clicked, installs malware on the victim's device, allowing the attacker to steal information or gain control of the device.
As attackers continuously develop new methods to exploit trust, it's essential to approach any unexpected or unsolicited message that asks for sensitive information or urges you to click a link with caution.
The mechanics of smishing
Smishing leverages social engineering, manipulation, and deceit to coerce victims into disclosing sensitive information. With people generally placing more trust in text messages than emails, fraudsters have increasingly turned to SMS for their schemes.
Here’s a step-by-step look at how a typical smishing attack unfolds:
- Crafting a persuasive message: The attacker begins by creating a deceptive SMS text message that mimics a legitimate institution, such as a bank, government agency, or well-known company. The message is designed to create a sense of urgency or fear, prompting the recipient to act immediately.
- Distributing the message: The fraudulent message is then sent to the target. To enhance credibility, the attacker may spoof the sender's phone number or name, making it appear as though the message is coming from a trusted source.
- Instilling a false sense of urgency: The message typically urges the recipient to take quick action to avoid a negative outcome. For example, it might warn that the recipient’s bank account is about to be suspended or that their credit card information needs to be verified.
- Offering a phony solution: The message often includes a link or asks the recipient to reply with personal information. The link may direct the victim to a fake website designed to look like a legitimate one, where they are prompted to enter sensitive information such as usernames, passwords, or credit card details.
- Harvesting personal data: Once the victim provides their information on the fraudulent site, the attacker collects this data, which can then be used for identity theft, financial fraud, or other malicious activities.
- Installing malware: In some instances, clicking on the link may also result in malware being downloaded onto the victim’s device. This malware can give the attacker ongoing access to the device and its data, further compromising the victim's security and privacy.
The success of smishing largely depends on the victim's trust in the message's source and their response to the urgency it conveys. By understanding these tactics, individuals can better protect themselves from falling prey to such attacks.
Understanding smishing attacks
A smishing attack is a form of cybercrime where malicious actors use deceptive SMS text messages to trick individuals into revealing sensitive information, such as passwords, credit card numbers, or other personal data. This type of attack takes advantage of the inherent trust people often place in text messages.
In a smishing attack, the criminal sends a text message that appears to be from a credible and trusted source, such as a bank, government agency, or reputable business. The message typically conveys a sense of urgency, claiming that immediate action is required to prevent serious consequences. For example, the text might warn that your bank account will be frozen unless you verify your banking details right away.
These messages often include a link to a fraudulent website designed to closely resemble the legitimate site of the organization being impersonated. When victims click on the link, they are directed to the fake site and prompted to enter their personal information, which the attacker then captures for malicious use. In some cases, clicking the link might also lead to the installation of malware on the victim’s device, allowing the attacker to steal information directly from the device.
Smishing attacks are increasingly common as they exploit the trust people have in SMS communication, making it essential to be cautious and vigilant when receiving unsolicited text messages, especially those that request personal information or urge immediate action.
How to safeguard yourself against smishing attacks
Protecting yourself from smishing attacks requires a mix of awareness, caution, and proactive measures. Here’s how you can defend against these deceptive schemes:
- Maintain a healthy skepticism: Always be cautious of unexpected text messages that ask for personal information or press you to take immediate action. If something feels off, it’s worth double-checking.
- Avoid clicking on suspicious links: Don’t click on links in unsolicited or unexpected text messages. If you think the message might be legitimate, independently find the contact information for the company and verify the request directly.
- Check the sender’s identity: Be wary of messages from unknown numbers or those that don’t appear as standard phone numbers. Scammers often use email-to-text services or other methods to obscure their real phone numbers, making the message appear more credible.
- Use security software: Protect your mobile device with reputable security software. Regularly update your device and applications to ensure you have the latest security patches, which can help defend against malware and other threats.
- Stay informed and educate others: Knowledge is a powerful defense. Familiarize yourself with common smishing tactics and share this information with friends and family to help them stay safe.
- Enable Two-Factor Authentication (2FA): Wherever possible, set up two-factor authentication on your accounts. This additional security step makes it more difficult for scammers to access your accounts, even if they obtain your login credentials.
- Do not engage with the message: If you receive a suspicious text, do not reply, even if it offers an option to “opt out” of future messages. Responding can confirm to the scammer that your number is active, potentially leading to more targeted attacks.
- Report suspicious texts: On most carriers, you can forward smishing texts to 7726 (which spells “SPAM”) to help them identify and block scammers. Additionally, in the United States, you can report smishing attempts to the Federal Trade Commission (FTC).
Above all, never share your personal information in response to unsolicited messages. If you’re ever uncertain about a request, it’s always safer to contact the company or organization directly through verified contact methods.
Common smishing attack scenarios
Smishing, a form of cybercrime that utilizes deceptive text messages, aims to trick recipients into divulging sensitive information, downloading harmful software, or visiting malicious websites. Below are five typical examples of how smishing attacks are carried out:
- Fake bank fraud alert: In this scenario, you receive a text message that seems to be from your bank, warning of suspicious activity on your account. The message urges you to verify your identity by clicking on a provided link and entering your account details. This link, however, leads to a fraudulent site designed to steal your information.
- False missed delivery notice: You might get a text claiming to be from a delivery service like FedEx or DHL, informing you that you’ve missed a package delivery. The message prompts you to click a link to reschedule the delivery, which typically asks for personal information or a small fee, both of which end up in the hands of scammers.
- Bogus account verification request: A message purporting to be from a popular online service, such as Amazon or PayPal, tells you there’s an issue with your account. The text instructs you to follow a link to verify your account details. This link leads to a fake website where any information you enter is captured by the attackers.
- Fake tech support alert: In this scenario, you receive a text warning that your computer has been infected with a virus. The message, supposedly from a well-known tech company, urges you to install an “antivirus” by clicking on a link. Instead of genuine antivirus software, the link downloads malware that compromises your device.
- Phony gift card winner notification: You receive a congratulatory message claiming that you’ve won a significant gift card from a popular retailer. To claim your prize, the text instructs you to click a link and provide personal details for verification. The link, however, leads to a scam designed to harvest your information.
These examples demonstrate the various tactics scammers use to exploit victims through smishing. It’s important to remember that legitimate organizations typically do not request sensitive information via text message. Always approach unsolicited messages with caution, especially those that create a sense of urgency or ask for personal data.
Additionally, because phishing attacks rely heavily on social engineering and deception, it’s crucial to stay vigilant and skeptical of any unexpected or suspicious messages that request personal information, prompt you to click on a link, or ask you to download an attachment.












































